The ubiquitous application programming interfaces, or APIs, continue to be the security bugbear of companies even as they are almost indispensable. Up to 75% of all credential abuse attacks against the financial services industry targeted APIs directly, according to a new report from Akamai Technologies, Inc.
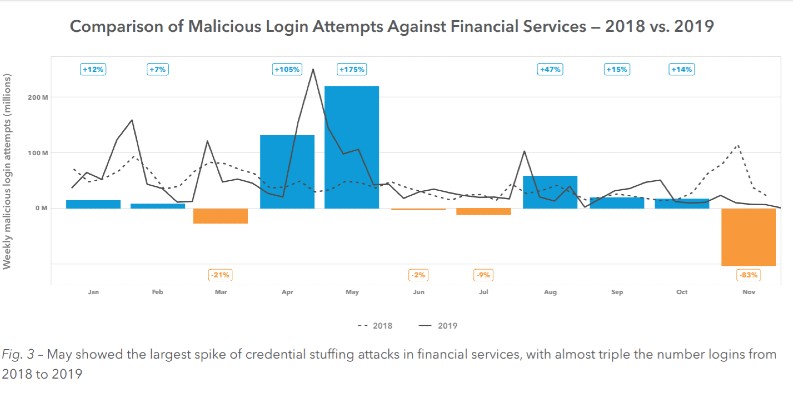
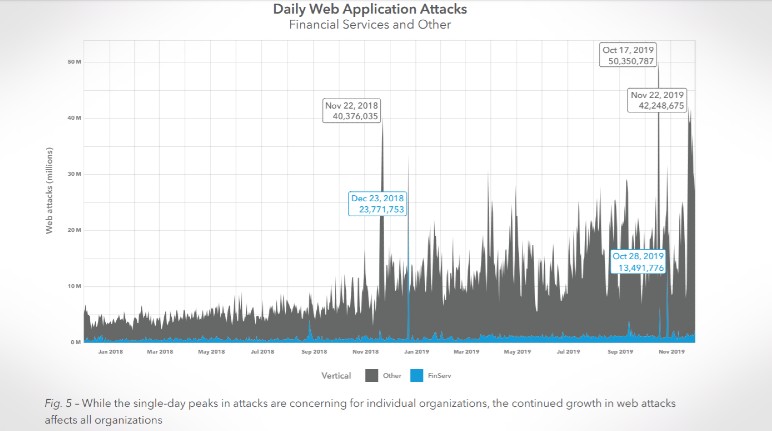
Akamai observed 85,422,079,109 credential abuse attacks from December 2017 through November 2019. Nearly 20%, or 16,557,875,875, were against host names that were clearly identified as API endpoints. Of these, 473,518,955 attacked organizations in the financial services industry.
Similarly, the Enterprise Strategy Group (ESG) notes that while cloud data protection services continue to become mainstream, strong APIs, application security frameworks, and a DevSecOps strategy are badly needed to secure data.
The report, which examined the SOAP (Simple Object Access Protocol) and REST (REpresentational State Transfer) communication methods for APIs, points out that criminals need three things to start staging credential stuffing campaigns.
- Credential lists (also known as combo lists), which contain usernames and passwords.
- A known target with accessible authentication mechanisms. In many cases, these authentication mechanisms are API endpoints.
- A tool to leverage those lists, as well as configuration files, to properly communicate with the victim’s authentication mechanism.
Various methods to expose data
Not all attacks were exclusively API-focused, according to the Akamai 2020 State of the Internet / Security: Financial Services – Hostile Takeover Attempts report published on Wednesday. Criminals continue to seek to expose data through a number of methods.
SQL Injection (SQLi), for instance, accounted for more than 72% of all attacks when looking at all verticals during the 24-month period observed by the report. That rate is halved to 36% when looking at financial services attacks alone. The top attack type against the financial services sector was Local File Inclusion (LFI), with 47% of observed traffic, the report notes.
LFI attacks exploit various scripts running on servers, and as a consequence, these types of attacks can be used to force sensitive information disclosure. LFI attacks can also be leveraged for client-side command execution (such as a vulnerable JavaScript file), which could lead to Cross-Site Scripting (XSS) and Denial of Service (DoS) attacks.
XSS was the third-most common type of attack against financial services, with a recorded 50.7 million attacks, or 7.7% of the observed attack traffic. The report also reveals that criminals continue to leverage Distributed Denial of Service (DDoS) attacks as a core component of their attack arsenal.
Crux of the issue
- The inconsistency in development methods using APIs has led to many of the problems seen over the past few years, according to the report. For example, some APIs allow as many password guesses as needed to successfully authenticate, while others throttle attempts.
- Another API development practice that leads to problems is related to error checking. Criminals leverage APIs to validate their lists and confirm that a username actually exists on a service. Depending on how the application or platform was developed, the error responses can be used to sort and validate
lists, which enables a higher degree of targeting. - Finally, API usage and widespread adoption have enabled criminals to automate their attacks. This is why the volume of credential stuffing incidents has
continued to grow year over year, and why such attacks remain a steady and constant risk across all market segments, the report notes.
Zero Trust model
The Akamai report recommends the Zero Trust model, wherein the network cuts off all access to network resources until it determines who the user is, and whether they’re authorized. The report acknowledges that Zero Trust is not a silver bullet. However, it believes that as adoption of this framework spreads, it will become more difficult for criminals to use passive attacks, like credential stuffing, to gain a foothold on a given network. It will be harder for them to leverage phishing or custom command and control servers, since DNS can be blocked at the source.
